Some of you may be aware of the excellent book by James Rickards, ‘The Road to Ruin’ in which he postulates the outcome of the next global financial crisis – if approached by the ‘Global Elites’ in a certain way. The way, he suggests, to deal with any virulent pandemic is to either create the antidote or, in its absence, the virus needs to be quarantined.
Through the economic jigs and reels of Neo Keynesian ‘interventionism’ versus Friedman’s monetarist, ‘laissez faire’ view, Rickards uses the basic thesis of a novel called ‘Cat’s Cradle’ to make his point. The author of that book creates a substance call ‘Ice Nine’ – a solution that rearranges the molecules in water, rendering anything it touches to ice, irrespective of the prevailing air temperature. It was no coincidence that this dystopian novel was written in 1963, just after the Cuban Missile crisis – the ‘Nuclear Winter’ scenario.
The point is; the smart move is to isolate the cause of the virus (rather than its effect) – until an antidote is discovered.
Our industry is going through turbulent times currently – our own global crisis. With mobile customers having to run the gauntlet of ever-increasing types of fraud, the Network Operators are naturally concerned about consumer harm – and it shows… Rather than approaching the problem in a unified way – that targets the problem at source (i.e. the rogue Affiliates perpetrating the fraud), the Mobile Operators are mandating sweeping changes with abandon. These changes not only profoundly damage revenue lines of the majority of well-intentioned actors in the value chain, but also stymie progress in the on-going battle for market share against non-mobile payment tools.
Whether it’s banning traffic sources, increasing hurdles to payment flows (PIN, Captcha…) or excluding certain types of services from being billed on their networks, these knee-jerk actions are in danger of throwing the proverbial baby out with the bath water. Granted, a small percentage of consumers are being billed without their consent or knowledge – and yes, the majority of advertisers are also unaware and helpless in the face of it, but is a ‘gun-shot’ reaction appropriate when a more specific ‘rifle’ solution would deal with the issue more effectively – and with far less co-lateral damage?
The problem is the Mobile Networks are desperate to protect their brand names – which is understandable considering that the source of most of their bad press (mobile billing) represents a tiny percentage of their overall revenue. However, actions are being taken by the VAS/wholesale middle management, who, under threat from senior management, have ‘consumer satisfaction scores’ and complaint levels as their KPIs – rather than revenue/innovation.
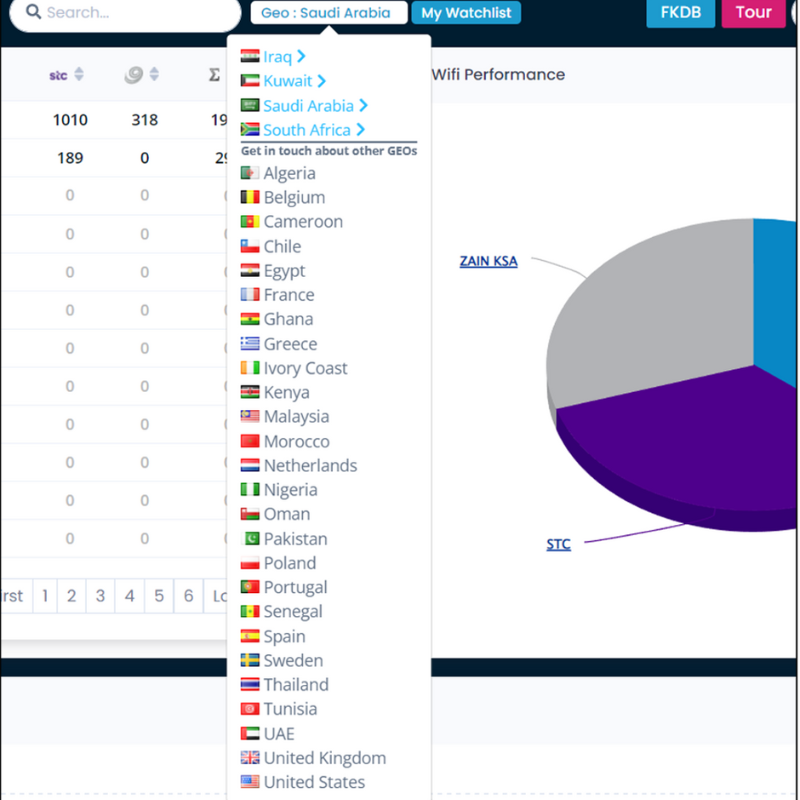
Fraud, like any virulent pandemic, is a universal issue – once a particular variant of an APK file leads to a successful auto-subscription works in one territory, this is quickly exported worldwide via surreptitious trading exchanges to local bad actors who know how to monetise in their local geo.
And the reaction from Mobile Networks is also a universal problem – the only difference being the voracity of their reaction varies from territory to territory. Indeed, there seems to be a regional paradigm to the reaction – which makes sense as Mobile Operator group ownership tends to be regionally based. MENA, for instance, is a good case in point. The likes of Viva, Etisalat, Zain and Ordedoo are all very strong in the region – hence group HQ dictats prevail and bad news travels a lot faster…
So back to Rickards’ thesis…. how do we isolate the source of the problem whilst minimising the co-lateral damage to the value chain? Clearly, there is no panacea but the following blueprint will help:
- Discover and capture as many fraud instances as possible in order to track trends through data analytics.
- Identify the various flow participants and in particular the responsible affiliates (easier said than done as they constantly change their IDs). To do this effectively requires close value chain collaboration.
- Quarantine them by exclusion from white list of ‘accredited sources’
- Reward advertisers who use only these sources by allowing them access to a more frictionless click payment flow rather than OTP/Captcha barriers.
- Advertisers can clean their own affiliates lists via the official accredited white-list (without accessing it as all will want to protect their successful, ‘clean’ sources).
- Implement a real-time anomaly detection tool which identifies fraud ‘live’ and gives advertiser option to reject source. Whether rejected or not, monitoring system will provide proof of maleficence (or otherwise) and take appropriate action with whitelist.
- Continually monitor these accredited sources in the wild – and alter their accreditation status up/down dependent upon their record.
Whilst I would follow Friedman’s economic ‘laissez faire’ view more easily than Keynes’ interventionist view, there are times when a proactive, harmonised industry step benefits the whole value chain in the long run.
Declan Pettit is Commercial Director of MCP Insight. They specialise in monitoring and anti-fraud solutions in Mobile billing industry.