Cybercriminals and fraudsters are using malicious apps for various nefarious purposes. Every month we hear of new attacks and threats, such as the recent revelation from cybersecurity research firm, ESET, that 12 Android apps were carrying malicious code as part of a sophisticated social engineering campaign.
In the mobile value-added services (mVAS) and direct carrier billing (DCB) space, the rise of malicious apps is also a problem. These malicious apps infiltrate reputable platforms like the Google Play Store, exploiting the trust of millions of users worldwide. Once downloaded, they silently execute their agendas, subscribing users to unwanted services and levying unauthorised charges on their mobile accounts. These actions occur clandestinely, with users unaware of the malicious activities unfolding in the background until they receive inexplicable charges on their mobile bills or deplete their credit.
The Mechanics of Malicious Apps in mVAS/DCB
Operating behind the scenes, malicious apps take actions from remote servers controlled by fraudsters, executing commands unseen by the mobile device owner. They navigate through the digital landscape, opening URLs and entering users’ mobile phone numbers to subscribe them to services, all while intercepting and deleting confirmation SMS messages to evade detection.
To illustrate how malicious apps operate within the mVAS/DCB ecosystem, we’ve created a video. Watch below to see what happens when a consumer downloads a malicious app onto their mobile phone.
The Consequences for Mobile Network Operators
For mobile network operators, the proliferation of malicious apps spells trouble on multiple fronts. Fraudsters are relentless in their pursuit of new tactics, leveraging social engineering and other deceptive strategies to lure users into downloading their apps or infecting legitimate apps with malware. As a result, operators can be inundated with complaints and refund requests from customers who have fallen victim to these activities, raising red flags with regulatory authorities and damaging their reputation in the process.
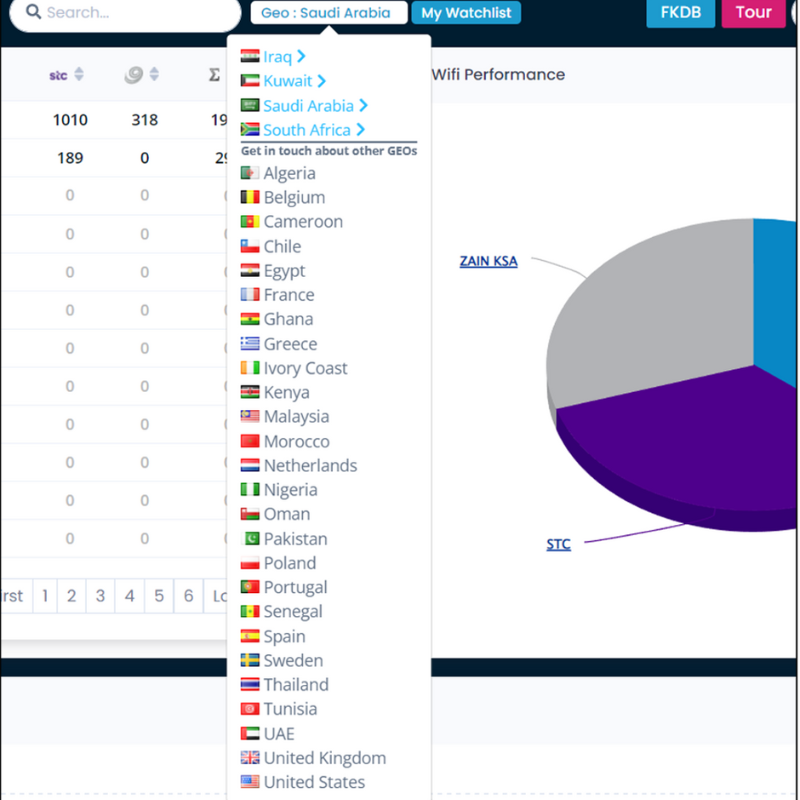
In the face of this ever-evolving threat landscape, mobile network operators must arm themselves with robust anti-fraud solutions. By leveraging advanced technologies that identify suspicious behaviour and detect non-human interactions, operators can effectively quarantine and block fraudulent transactions, safeguarding their customers and preserving the integrity of their business. These proactive measures not only protect against financial losses but also shield operators from reputational damage and regulatory scrutiny.
If you would like to find out more about how MCP SHIELD can protect your customers and your mVAS/DCB revenue streams, contact the MCP team here.
For consumer advice on how to identify malicious apps on the Google Play Store, read our blog post and feel free to share with your customers.