says MCP’s Declan Pettit | 24 November 2017
Fraud technologies are being democratised worldwide at a frightening pace, making it possible for anyone with a laptop, loose morals and a passing technical knowledge to defraud mobile customers.
The good news, for those of us who dislike traipsing around the High Street during the festive season, is that on-line shopping is expected to exceed retail shopping for the first time ever. The tools have developed to such an extent that, within a few minutes – on any mobile device – you can buy and organise delivery for anything, with a single click.
The downside is the stakes are higher than ever for anyone buying or selling on-line because the fraudsters’ playing field is a lot larger and the rewards have grown exponentially.
What’s been going on?
Mobile commerce has gone from a measly 4% share of the market at the end of 2010 to a 21% share at the end of 20161, indicating a substantial change in user behaviour and, as with all proliferations, this raises new problems for on-line user verification.
Most recently we have seen application installation packages (APKs) under attack from increasingly sophisticated Adware viruses, immune to factory resets. These viruses can install third party apps, activate subscriptions and make one-off purchases on a user’s device. ‘Bot networks’ aren’t going anywhere either; fraudsters are getting better at building these across unsuspecting users’ devices (generating background fake clicks).
Recently, at Monitoring Compliance Partners (MCP) we have been focusing on detection methodologies and, supported by our newly formed Special Ops Team, we can now detect anomalies, giving our clients the tools to block a flow if it is deemed fraudulent. On-going analysis is beginning to drive significant results and understanding for our clients including Network Operators, Regulators, Payment Aggregators and Merchants around the world. We have also initiated a PEN testing programme – working with clients to penetrate test platforms for security weaknesses in order to provide prevention solutions.
What are Bots?
Bots are probably the most useful tools in the fraudsters’ arsenal with bot generated traffic surpassing that of humans for the first time ever last year according to Incapsula.2 It isn’t all bad – not all bots are created equal, some are ‘naughty’ and some are ‘nice’. Search engine spider bots are ‘nice,’ Instant Messaging bots are annoying but ‘nice’; and the bots built by cyber criminals to use as powerful tools against online merchants are definitely ‘naughty’ and getting naughtier.
Bots are created to complete online tasks much faster than humans ever could by running automated scripts. The latest ‘Gen4’ Bots have reached a level of sophistication where their ability to mimic human online behaviour makes them harder to detect, allowing the bad ones to infect browser extensions more easily and to latch onto real users’ identities and systems through various tactics such as Scalping or Hoarding and Account Takeovers.
For Scalping, attackers programme bots to rapidly buy up a product so that they can be resold for a quick profit elsewhere. Big releases of popular products are often a target and as much as 90% of traffic in these cases may be produced by bots. This was the case for the Super Nintendo NES Classic Edition earlier this year. The re-sell price was up to triple the list price!3 Account Takeovers are achieved by bots running ‘credential stuffing’ scripts against compromised lists of Usernames/passwords and then employing user data to make purchases on sites where the user has shopped.
It is no wonder that bot fraud is expected to cost online advertising $6.5 billion in 2017, according to the Association of National Advertisers.4
Are Carrier Billing Services being affected?
All on-line advertisers are well aware of the current scourge of Install fraud and Click fraud mechanics – Bot attacks which fool the Advertiser’s metrics into attributing ‘fake sales’ to these rogue Affiliates. Indeed, this is not limited to browser environments. Fake in-app Purchase receipts (allegedly from the real app store) can be used to trick the app into thinking a purchase has been made, therefore skewing app metrics against the advertiser.
Most disturbing of all is how the fraudsters are now using Bot attacks to make money through Carrier Billing. As more people use smartphone apps to make purchases online, attacks through carrier billing are proliferating within App store environments and in particular on devices using Android’s OS. So now fraudsters are bringing the fight to consumers directly. Examples range from ‘fake payment requests’ into payment gateways to sleeper APK files that have been downloaded and only come to life when they have been installed. Even then, unauthorised billing can occur over a period of time in order not to arouse suspicion.
Any Good news?
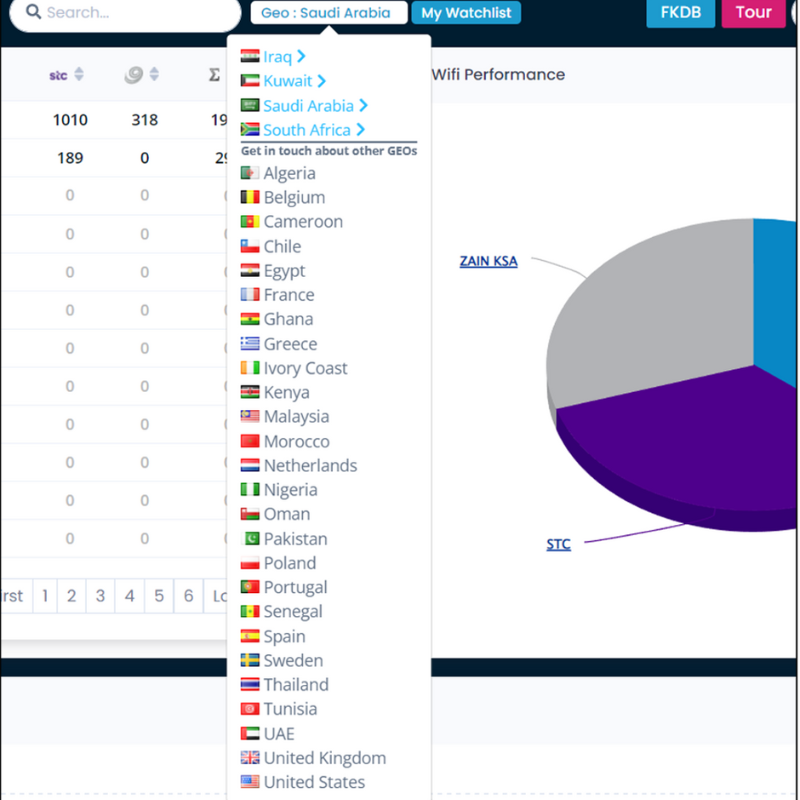
Despite their best efforts, bots eventually start displaying suspicious behavioural patterns that can uncover spoofed IPs or emulated devices. Engaging with compliance companies like MCP and employing our VERISCANNER toolset will help identify these anomalies.
VERISCANNER uses live metrics – starting at a user’s very first click – to identify fraudulent flows in the advertising environment. Our intelligent ad crawler and compliance checking procedures continue to develop quicker methods for fraud pattern detection. Plus, coupled with our best practice compliance alert protocol, we host a number of block lists (in particular for children’s environments) that are shared throughout the industry.
For the qualitative identification of fraud, there is still no substitute for human analysis of your campaign to augment the automated process. Besides, we still need people on the ground to ensure lines of communication are maintained across the whole value chain. Working with MCP will provide you with that qualitative insight and will also simplify the process of working with your advertising partners to combat fraud.
It won’t be resolved by Christmas – but working together is the first stop in stemming this fraudulent tide.
Contact: declan@mcpinsight.com
References